Containerization
Containerization
If an employee leaves the company or a device is lost or stolen, corporate data inside the Secure.Systems™ container can be remotely erased without infringing upon the employee’s personal data.
Categories: Cyber Security
Tag: Cyber Attack, Cyber Solution
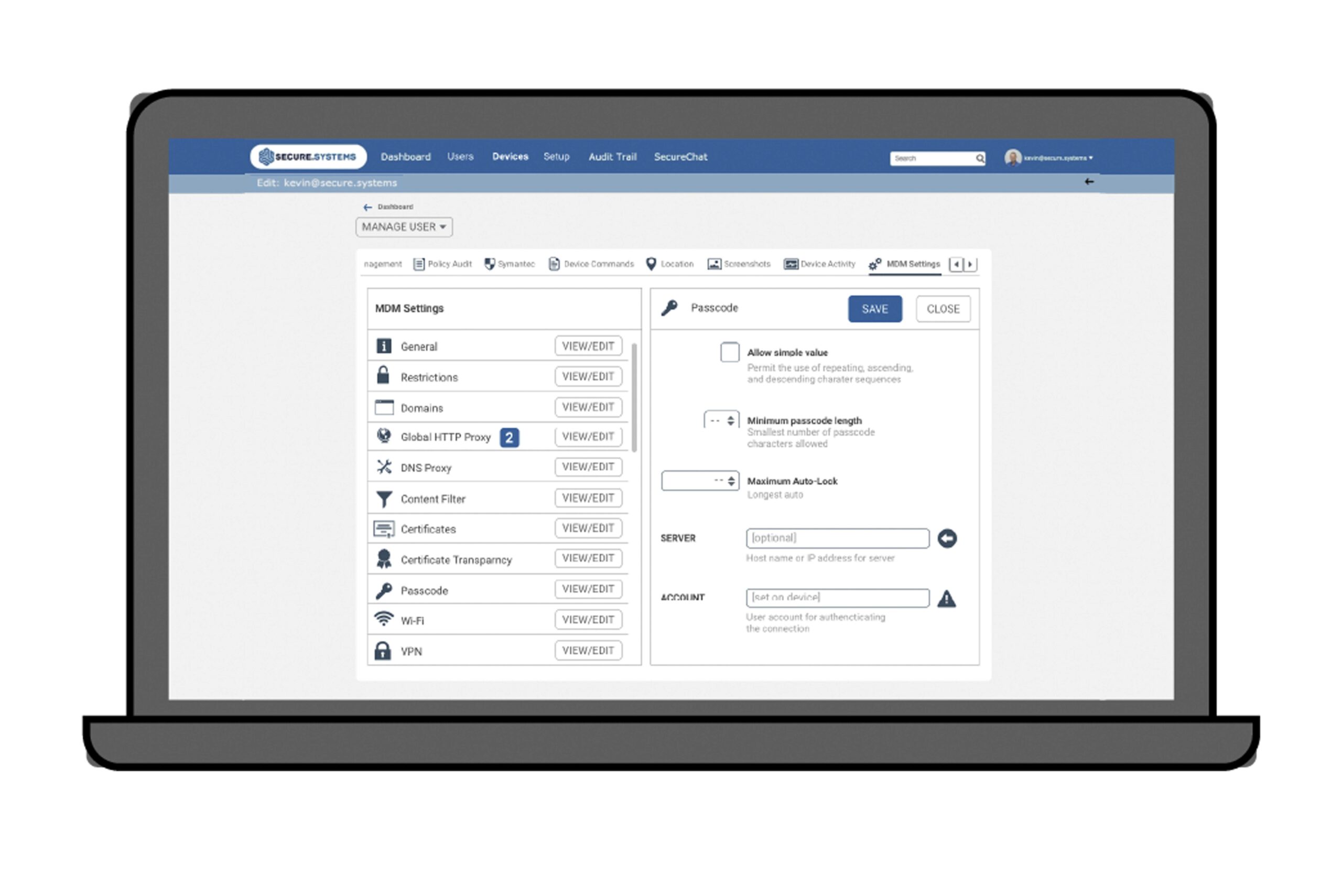
Administrators, employees and compliance managers all benefit from the easy management of Secure.Systems™. Privileged users can easily define the security rules within the app and also grant or deny corporate data access privileges on devices.
Integrate all your devices from mobile (iOS and Android) to desktop (Mac and PC) with our virtual container solution. Implementation involves using an open source virtual machine to create a separate container on your devices. With our custom encryption, we protect the virtual hard disk and transport it on the virtual machine. Once the container is provisioned, it will install the encrypted virtual machine which you can then log into just like a separate desktop within your normal computer. You may install programs, save files, and use applications just as you normally would, knowing that your data is completely secure. It’s that easy.
Please click for the brochure


