PenTest (Penetration Test)
PenTest (Penetration Test)
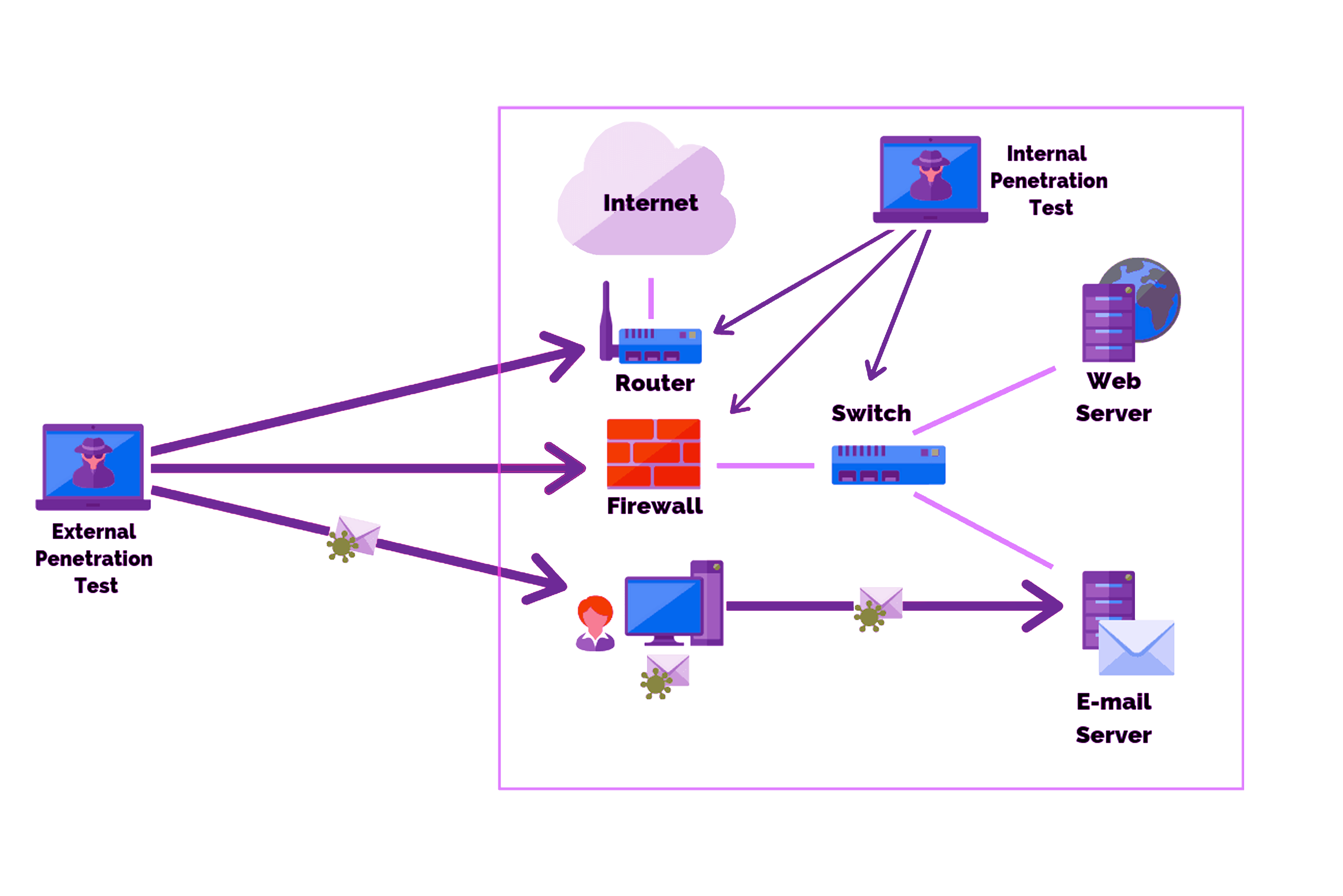
PenetrationTest, known as PenTest, is basically a special testing process that requires advanced engineering that includes scanning, analyzing, infiltrating and tightening all the building blocks of an information system against possible cyber attacks.
During testing, experts act like an attacker and expose all the vulnerabilities, risks and accessibility of the system. Since there are many different methods and variables, the penetration test should be performed by experts.
Categories: Cyber Security
Tag: Internal and External Cyber Threat, Red Team, Red Team, Infiltration Detection, Pen Testing, Penetration
WHY PENETRATION TEST IS IMPORTANT
The ultimate goal of PenTest is to reveal how secure your system infrastructure is from the perspective of an attacker and to close any vulnerabilities.
In addition to identifying weak points in an organization’s security posture, measuring the appropriateness of its security policy and to determine the extent to which the organization applies cybersecurity principles.
The most basic thing to remember is that all systems are vulnerable to attack.
No system is 100% secure. For these reasons, it is very important for organizations to have their systems regularly PenTested and to pass security patches to the operating system and applications in a timely manner.
Penetration Tests are basically divided into three stages;
Black Box:
In this method, no information is requested from the institution where the pentest will be carried out, thanks to the studies and completely manual methods.
The attempt is made to infiltrate the system from the interfaces that are open to the internet or not. In this way, the general analysis and vectors of threats that the organization may receive from outside are extracted.
The Black Box method is the closest test method to a real attack scenario from the outside. The biggest goal is to infiltrate the database in the target system.
Gray Box:
Thanks to this test, the danger surface of the system is analyzed by using the gaps of the system by coming as a guest inside the institution. In this way, many processes from the attacker’s transition to the existing system, access to databases, and dominance over applications are handled through this test.
The Gray Box method reveals how successful an attack by a hacker who can physically enter the organization can be. The greatest goal is to take over the entire system, even with limited authority.
White Box:
With this test, the security specialist requests a definition of a standard user from the institution where the test is performed, so that as an expert standard user, it is checked whether he has increased his rights on the system and his dominance over databases and all other informatics infrastructure. During these tests, various tools are used, as well as special manual methods, including the necessary techniques to prevent the system from catching the attacker.
The White Box method reveals how effective an internal attack on the organization can be.
In the penetration tests we have conducted in the last two years, there has been no institution/company (including only 5-6 computers) whose systems we could not infiltrate, especially in the gray stage.
PENETRATION TEST STAGES:
Penetration Testing is a process performed with a certain systematic approach. Penetration Test/Security Test used by ÖLÇSAN, Cyber Security and Artificial Intelligence, OSSTMM (Open Source Security Testing Methodology Manual) v3 Open Source Security Testing Methodology Manual, OWASP (Open Web Application Security Project) Testing Guide 4.0 and It is based on NIST 800-115 (National Institute of Standards and Technology-Technical Guide to Information Security Testing and Assessment) methodologies.
- Passive Information Gathering (Tracking):
The scope of testing and objectives are defined, including the systems to be considered and the test methods to be used.
This stage includes information such as domain names, network blocks, routers, IP addresses, and employee information within the target system infrastructure and scope,
It is the step that provides information about all kinds of details that will contribute to the success of the attack, such as phone numbers.
This information gathered from open sources can often contain surprisingly critical information. For this purpose, many resources are used, especially the target institution’s website and social media platforms.
- Active Information Collection and Scanning:
It is possible to prioritize with the help of the information obtained in the first stage, at this stage, in which active and passive devices are determined to be live within the detected IP range.
At this stage, it is important to obtain operating system, open ports and services and their version information on the detected live systems.
In addition, if it can be listened to, network traffic is also monitored and critical information about the system infrastructure is tried to be collected as much as possible.
- Casting Extraction:
After understanding how the target application will respond to various intrusion attempts, in this step, active connections are established with systems that are detected to be alive and direct inquiries are made.
In other words, this stage; It is the stage where services such as ftp, netcat, telnet are used effectively and interacted with target systems.
- System Hijacking
All the information obtained in the previous stages has a single purpose. Gaining unauthorized access to the target system, reading the database or accessing information that should not be accessed.
This stage; This is the step where exploitation methods that can be applied in the light of the operating system running on the target system, the open ports and the services serving on these ports and their versions are tried and infiltrated.
Web-based portals and applications, in particular, have a special position because they are both outward-facing windows and can host a large number of attack vectors.
It requires serious expertise and experience to be able to use the existing exploitation methods successfully and flexibly, without damaging the system, without leaving any traces, during the process of taking over the system. This phase of PenTest is therefore the most important and critical step.
- Authorization Upgrade
A system is only as strong as its weakest link. System access, which is achieved in some way, usually takes place with a low authority in the first step. At this stage, the PenTest specialist aims to increase his authority to the administrator level by taking advantage of the vulnerabilities in the operating system or environment, and then to seize other devices in the network environment with these additional powers and finally to seize the highest level user privileges such as Domain Administrator or Database Administrator. .
PENETRATION TEST SERVICE AND AFTER:
As a result of the penetration test, the security vulnerabilities detected in the target systems by our company and how these vulnerabilities were exploited are included in the “Penetration Test Result Report”, which is presented with sample screen prints. The final report also includes a solution proposal on how to close each gap.
As a cyber security firm; We do not specifically sell products in terms of the sensitivity, independence and health of the penetration tests we conduct. However, if requested, we also provide secure network installation and design consultancy services to make systems more secure.
Our Incedent Repsonse solutions are an incident response platform that automates the analysis of the current cyber attacks before, during and after the attack by reducing them to minutes. With its easy installation and integration features, it reduces the need for experienced personnel by ensuring that institutions get maximum efficiency from the security products they have already invested in.
- Automatically highlights the points that need to be prioritized with the Patrol feature.
- Reduces evidence collection time to 5 minutes, which can take hours or even days.
- Provides time independent, fully automatic event response with SIEM/SOAR/EDR integration.
- It enables the creation of an attack or alarm timeline within minutes without exceeding the 72-hour notification period in KVKK.
- It reduces the need for personnel by automatically enriching the alarms received by the Cyber Operations Centers.
- It allows you to examine in detail the CTI reports regarding the valuable data sold on the DarkWeb for your institution.
- It allows you to hunt threats with triage profiles on all your endpoints.
- With easy and understandable reporting, it offers the opportunity to examine the evidence immediately without the need for parcel processing.
References:
1.OSSTMM (Open Source Security Testing Methodology Manual) v3 Open Source Security Testing Methodology Manual
2.OWASP (Open Web Application Security Project) TestingGuide 4.0
3.NIST 800-115 (National Institute of Standards and Technology – Technical Guide to Information Security Testing and Assessment)


