T-STRAINER

T-STRAINER
T-STRAINER is an intrusion detection and prevention system. Intrusion detection and prevention systems ensure network security. Intrusion detection systems (IDS) are one of the important security components, covering methods that monitor the activities occurring on the network and analyze the traffic for the detection of possible attacks, violations and threats. Intrusion prevention systems (IPS) are network security systems that cover the detection and prevention of attacks.
Categories: Cyber Security
Tag: IDS, IPS, Intrusion Detection System, Intrusion Prevention System, Packet, Protocols, Network, Network Security, Data Security, Security, Intrusion Detection, Packet Analysis
T-STRAINER, an intrusion detection and prevention system (IDS/IPS), is a network security system that continuously monitors a network for malicious activity and attacks and prevents this attack, including reporting, blocking or disabling when an attack occurs.
The fact that networks have a complex structure, that they are connected to other networks, especially the Internet, with many access points, that cyber attacks are diversifying and increasing day by day, at the same time, realities such as these complex network systems can no longer be protected only with encryption or firewall, network traffic is constantly monitored and made real-time detection of attack attempts inevitable. Contrary to other network security technologies, T-STRAINER is efficient enough to scan high volumes of traffic with minimal impact on network performance, is a user-friendly application with an expandable and customizable signature list, configurable operating modes and interface possibilities.
Advantages
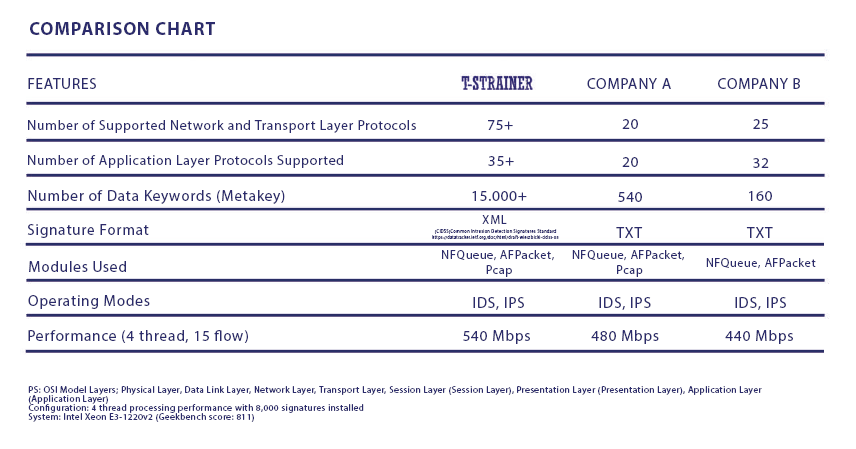
- It supports much more protocols and metakey information of these protocols than other applications like T-STRAINER. By using this metakey information, it offers wider and more comprehensive network security.
- The user can go beyond the accepted signature rules with the number of supported metakeys. Thus, the user can create new rules for himself.
- Unlike other commercial and open source products, it uses the standard CIDSS* signature format. Full translation of some standard accepted signatures to another system is impossible, but ali signatures can be translated to CIDSS. Thus, ease of use is provided.
- It allows the user to easily create new signatures from the interface. in this way, the user can create their own signature rules with the options offered from the interface without having to write them in accordance with the format. Created signature rules are automatically converted to CIDSS format.
- It offers the advanced technological features of the product to the user with an easy-to-use interface.
Abilities
- High Availability
- SOC Integration
- IP Reputation
- Optimized for speed with minimal resources
- Current Signatures
- Automatic Update
- Metakey Based Rules
- Multithread Operation
- DDOS Protection
- Network Security
- WEB Application Security
- Database Security
- Network Visibility
- Traffic Logging
- Management Platform
- Quick and easy installation
- It is easy integrated with other applications, works commercially and open source.